Online shopping with a VPN: Find deals and protect yourself this...
Stand aside, brick-and-mortar stores: Online shopping has been growing exponentially, bringing with it undeniable upsides, but also a few...
How brute-force cracking might reveal your password
In cryptography, a brute force attack attempts to decipher encrypted content by guessing the encryption key. This attack is...
The secret codes that nobody can crack
Remember back in school, when you and your best friend would exchange secret notes across the classroom in code?...
5 most shocking cyber scams of 2017
The results are in and 2017 is already being called the worst year in terms of cyber scams. Where...
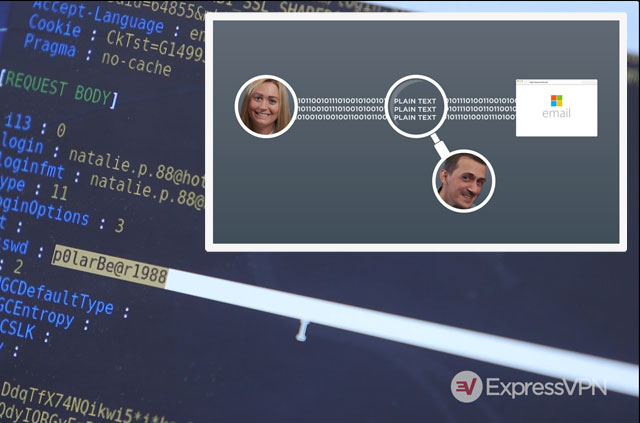
Wi-Fi hacking explained: SSL stripping
“How to stay safe online!” is a common headline these days. We are told repeatedly that free public Wi-Fi...
Here’s what happens when companies fail to put privacy first
You could easily call 2017 the year of the leaks. With so much sensitive and potentially incriminating evidence hitting...
Your YouTube history exposed: Researcher identifies inherent security flaw in video...
This post was originally published on March 22, 2017.
While researching how Internet Service Providers (ISPs) could optimize their services...
I’m sorry, Dave. I’m afraid I can’t do that: When virtual...
The Wall Street Journal estimates that one million IoT devices were recently used by hackers to carry out a...
Unhackable notifications: It’s easy to encrypt Facebook with a PGP key
Your Facebook account is valuable. It contains private chats, a list of your personal connections, and, if you use...
The Siri-ous benefits and dangers of voice technology
“Hey, Siri”
Ask any iOS user if they’ve uttered the above, and they’ll share personal anecdotes of sketchy queries and...